View
Sorting
Products found: 81
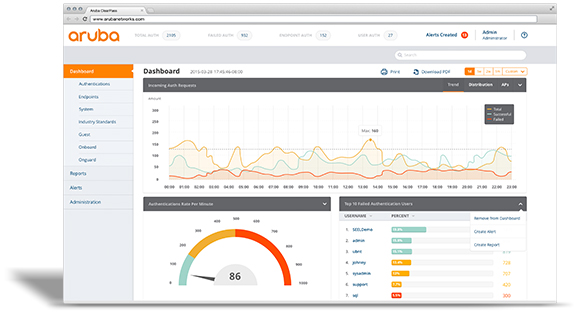
Aruba 200 Series Access Points
The AP-205 and IAP-205 models feature four integrated omnidirectional downtilt antennas, while the AP-204 and IAP-204 support external detachable dual-band antennas using two RP-SMA antenna connectors. UNIQUE BENEFITS
Wi-Fi client optimization
- To eliminate sticky client behavior while users roam, 200 series APs feature patented ClientMatch technology, which continuously gathers session performance metrics from mobile devices.
- If a mobile device moves away from an AP or if RF interference impedes performance, ClientMatch automatically steers the device to a better AP.
- ACC lets WLANs perform at peak efficiency by minimizing interference from 3G/4G LTE networks, distributed antenna systems and commercial small cell/femtocell equipment.
- The 200 series APs support priority handling and policy enforcement for unified communication apps, including Microsoft Lync with encrypted videoconferencing, voice, chat and desktop sharing.
Aruba 360 Secure Fabric
Aruba ClearPass
ClearPass allows you to safely connect business and personal devices to your network in compliance with your security policies. It allows you to grant full or limited access to devices based on users’ roles, device type, and cybersecurity posture.
This solution leverages the next plan:
Identify
With this new demand for network access, the burden on your IT department has increased exponentially and it’s not just laptops and smartphones that should be on your radar. IoT devices, printers, and even surveillance cameras are connecting to companies’ wireless networks.
ClearPass helps you identify which devices are being used, how many are connected to your network, where they’re connecting from, and which operating systems are supported. It gives you continuous visibility into changes on your network, including which devices are connecting and disconnecting.
When you need device-specific information, you can easily identify a device’s:
- Type and model name
- MAC address
- IP address
- NIC vendor
- OS and version number
- VLAN
Enforce
Enforcing network policies can pose a huge challenge to IT departments. When an employee wants to add a new device to the network, they often have to go through extensive IT protocols. They may even need someone from IT to walk them through the process.
ClearPass allows you to enforce policies during the onboarding of new devices without any involvement from your IT department – whether it’s a laptop, smartphone, or security camera. A built-in certificate authority lets you support devices more quickly without any additional IT resources.
Your IT team will simply need to establish your foundation of security and write rules that define:
- Who can onboard a device
- The type of device users can onboard
- How many devices each user can onboard
You can then enforce access a number of ways. You can use a portal, or you can use the more secure and preferred method that uses encryption in the authentication process. After devices are granted access, ClearPass uses active and passive profiling methods to monitor your network and keep it safe.
Protect
The health of individual devices connected to your network is an essential component of network security. With ClearPass OnGuard, your IT team can define the “level of health” a device must have in order to gain network access.
This solution automatically conducts critical endpoint health checks and posture assessments to ensure that all devices are compliant with your requirements (and industry best practices). It works for both wired and wireless networks.
ClearPass also offers a variety of third-party integrations (which we’ll touch on shortly). These integrations empower you to implement dynamic policy controls and threat remediation. You’ll have real-time insight into the activity on your network, equipping you to identify and address any threats that may present themselves.
After all, you have to be prepared to take action if you discover unusual network behavior. That requires establishing a unified approach that can block traffic and disconnect devices when necessary – even in the middle of the night.
Integrate
The right network security solution must be comprehensive and that often requires you to create a seamless solution comprised of several different platforms.
Aruba ClearPass Exchange integrates with over 25 IT partners – the vast majority of your current technology and security stacks - to ensure that every element of your system is working without issue.
These third-party technology systems could include:
- Firewalls
- Enterprise mobility management (EMM)
- Mobile device management (MDM)
- Security information and event management (SIEM)
Whichever platforms you use (or are considering), they will work with ClearPass’ REST-based APIs, Syslog messaging, and extensions repository. Your collective solution will deliver end-to-end policy enforcement and the visibility you need to keep your network secure.
Source: inbound.kelsercorp.com/blog/what-is-aruba-clearpass-and-how-does-it-protect-your-network
ClearQuest
ForeScout CounterACT
CounterACT agentless technology discovers, classifies and assesses devices. CounterACT interrogates the network infrastructure to discover devices as they connect to the network. Our customers have reported seeing up to 60% more devices on their network than previously known. After discovering a device, CounterACT uses a combination of passive and active methods to classify the device according to its type and ownership. Based on its classification, CounterACT then assesses the device security posture and allows organizations to set policies that establish the specific behavior the device is allowed to have while connected to a network.
At ForeScout, we don’t believe in artificial barriers that limit your options and force vendor lock-in. CounterACT works with leading network infrastructure, third-party security and IT management solutions. It also offers flexible deployment and configuration options to match your company’s specific needs. Choose physical or virtual deployments or both, and centrally manage them with CounterACT Enterprise Manager.
Several features set CounterACT apart:
- Agentless: No endpoint agents are required for authentication and network access control, allowing CounterACT to see and control managed, unmanaged and IoT devices.
- Open interoperability: CounterACT works with popular switches, routers, VPNs, firewalls, endpoint operating systems (Windows®, Linux, iOS®, OS X and Android), patch management systems, antivirus systems, directories and ticketing systems—without infrastructure changes or upgrades.
- Security orchestration: Optional modules orchestrate information sharing and policy-based security enforcement between CounterACT and leading IT and security management products.
- 802.1X authentication, or not: Choose 802.1X or other authentication technologies such as LDAP, Active Directory, RADIUS, Oracle and Sun. Hybrid mode lets you use multiple technologies concurrently.
Forescout Platform
Fortinet FortiCASB
FortiNet FortiClient
Fortinet FortiGate NGFW
Fortinet FortiGate SD-WAN
- Best WAN Edge Price/Performance
- WAN Path Controller with Remediation
- Fastest Application Identification and Steering
- Advance Routing Capabilities and WAN Optimization
Fortinet FortiMail Secure Email Gateway
- Top-rated Antispam and Antiphishing: Maintain productivity by shielding end users from unwanted spam and malicious phishing attacks
- Independently certified advanced threat defense: Thwart cyber criminals intent on stealing data, holding systems for ransomware, conducting fraud, and other malicious purposes
- Integrated data protection: Maintain the privacy of personal information and confidentiality of sensitive data in compliance with regulatory and corporate guidelines
- Enterprise-class management: Free staff and end users to drive the business by reducing the time spent on email administration
- High-performance mail handling: Speed the delivery of legitimate email at an affordable cost
FortiNet FortiNAC
- Network visibility to see every device and user as they join the network
- Network control to limit where devices can go on the network
- Automated response to speed the reaction time to events from days to seconds
Fortinet FortiSandbox
Fortinet FortiWeb: Web Application Firewall (WAF)
- Proven Web Application Protection. FortiWeb protects against all the OWASP Top-10 threats, DDoS attacks and many others to defend your mission critical web-based applications
- AI-based Threat Detection. In addition to regular signature updates and many other layers of defenses, FortiWeb’s AI-based, dual-layer machine learning engines protect against zero-day attacks
- Security Fabric Integration. Integration with FortiGate firewalls and FortiSandbox deliver protection from advanced persistent threats
- Advanced Visual Analytics. FortiWeb’s visual reporting tools provide detailed analyses of attack sources, types and other elements that provide insights not available with other WAF solutions
- False Positive Mitigation Tools. Advanced tools that minimize the day-to-day management of policies and exception lists to ensure only unwanted traffic is blocked
- Hardware-based Acceleration. FortiWeb delivers industry-leading protected WAF throughputs and blazing fast secure traffic encryption/decryption
FortiSIEM
FortiSIEM Delivers Next-Generation SIEM Capabilities
FortiSIEM brings together visibility, correlation, automated response, and remediation in a single, scalable solution. It reduces the complexity of managing network and security operations to effectively free resources, improve breach detection, and even prevent breaches. Product's architecture enables unified data collection and analytics from diverse information sources including logs, performance metrics, security alerts, and configuration changes. FortiSIEM combines the analytics traditionally monitored in separate silos of the security operations center (SOC) and network operations center (NOC) for a more holistic view of the security and availability of the business. In addition, FortiSIEM UEBA leverages machine learning and statistical methodologies to baseline normal behavior and incorporate real-time, actionable insights into anomalous user behavior regarding business-critical data. By combining telemetry that is pulled from endpoint sensors, network device flows, server and applications logs, and cloud APIs, FortiSIEM is able to build comprehensive profiles of users, peer groups, endpoints, applications, files, and networks. FortiSIEM UEBA behavioral anomaly detection is a low-overhead but high-fidelity way to gain visibility of end-to-end activity, from endpoints, to on-premises servers and network activity, to cloud applications.IBM AI OpenScale
- Open-by-design. Integrate with common AI tools, frameworks, and environments across public, private, or on-prem.
- Trust, transparency and explainability. Provide explanations into how AI decisions are being made, and automatically detect and mitigate bias to produce fair, trusted outcomes.
- Automation of AI. Automate the AI application lifecycle, from AI-generated neural networks tailored to your data and workloads, to de-biasing technology that mitigates bias at runtime.
- Understand how AI applications reach decisions – AI OpenScale explains how AI recommendations are made in everyday business terms.
- Address bias in AI applications automatically – AI OpenScale continually monitors AI applications and prevents bias through a unique, powerful and automated de-biasing technology.
- Ensure AI applications are auditable – AI OpenScale logs every prediction, every model version, and all the training data used, together with all metrics to help businesses comply with regulations such as GDPR.
- Use AI to build AI – AI OpenScale addresses the short supply of human AI engineers by throwing AI at the problem. IBM's Neural Network Synthesis Engine (NeuNetS) will allow businesses to rapidly and automatically build neural networks – essentially to run AI – from scratch. NeuNetS will initially be available in AI OpenScale in beta.
- Manage and scale AI in an interoperable fashion – AI OpenScale can work with open source machine learning or deep learning models, such as Tensorflow, Scikitlearn, Keras and SparkML. It can also handle applications and models trained and hosted on common environments, including IBM Watson, IBM PowerAI, Seldon, AWS SageMaker, AzureML and other non-IBM engines.
IBM BladeCenter
A web site called Blade.org was available for the blade computing community through about 2009.
In 2012 the replacement Flex System was introduced.
IBM BladeCenter (E) The original IBM BladeCenter was later marketed as BladeCenter E[3] with 14 blade slots in 7U. Power supplies have been upgraded through the life of the chassis from the original 1200 to 1400, 1800, 2000 and 2320 watt.
The BladeCenter (E) was co-developed by IBM and Intel and included:
- 14 blade slots in 7U
- Shared media tray with optical drive, floppy drive and USB 1.1 port
- One (upgradable to two) management modules
- Two (upgradable to four) power supplies
- Two redundant high-speed blowers
- Two slots for Gigabit Ethernet switches (can also have optical or copper pass-through)
- Two slots for optional switch or pass-through modules, can have additional Ethernet, Fibre Channel, InfiniBand or Myrinet 2000 functions.
IBM BladeCenter T
BladeCenter T is the telecommunications company version of the original IBM BladeCenter, available with either AC or DC (48 V) power. Has 8 blade slots in 8U, but uses the same switches and blades as the regular BladeCenter E. To keep NEBS Level 3 / ETSI compliant special Network Equipment-Building System (NEBS) compliant blades are available.
IBM BladeCenter H
Upgraded BladeCenter design with high-speed fabric options. Fits 14 blades in 9U. Backwards compatible with older BladeCenter switches and blades.
- 14 blade slots in 9U
- Shared Media tray with Optical Drive and USB 2.0 port
- One (upgradable to two) Advanced Management Modules
- Two (upgradable to four) Power supplies
- Two redundant High-speed blowers
- Two slots for Gigabit Ethernet switches (can also have optical or copper pass-through)
- Two slots for optional switch or pass-through modules, can have additional Ethernet, Fibre Channel, InfiniBand or Myrinet 2000 functions.
- Four slots for optional high-speed switches or pass-through modules, can have 10 Gbit Ethernet or InfiniBand 4X.
- Optional Hard-wired serial port capability
IBM BladeCenter HT
BladeCenter HT is the telecommunications company version of the IBM BladeCenter H, available with either AC or DC (48 V) power. Has 12 blade slots in 12U, but uses the same switches and blades as the regular BladeCenter H. But to keep NEBS Level 3 / ETSI compliant special NEBS compliant blades are available.
IBM BladeCenter S
Targets mid-sized customers by offering storage inside the BladeCenter chassis, so no separate external storage needs to be purchased. It can also use 110 V power in the North American market, so it can be used outside the datacenter. When running at 120 V , the total chassis capacity is reduced.
- 6 blade slots in 7U
- Shared Media tray with Optical Drive and 2x USB 2.0 ports
- Up to 12 hot-swap 3.5" (or 24 2.5") SAS or SATA drives with RAID 0, 1 and 1E capability, RAID 5 and SAN capabilities optional with two SAS RAID controllers
- Two optional Disk Storage Modules for HDDs, six 3.5-inch SAS/SATA drives each.
- 4 hot-swap I/O switch module bays
- 1 Advanced Management Module as standard (no option for secondary Management Module)
- Two 950/1450-watt, hot-swap power modules and ability to have two optional 950/1450-watt power modules, offering redundancy and power for robust configurations.
- Four hot-swap redundant blowers, plus one fan in each power supply.
IBM Blockchain
- Написание приложений с технологией блочной цепи с помощью Hyperledger Composer; Согласование бизнес-требований и технической разработки;
- Использование предпочтительнуой среду для превращения бизнес-правил в код
- Запуск новой сети и добавление других организаций-партнеров с простыми в использовании инструментами активации;
- Определяйте гибкие, демократические политики с редактором политики для регулирования изменений в сети;
- Управляйте многопользовательскими рабочими процессами с помощью панели действий участника, интегрированных уведомлений и инструментов для сбора защищенных подписи
- Мониторинг и управление сетевыми ресурсами со встроенными панелями мониторинга;
- Защита сети с упрочненной инфраструктурой безопасности с 100% -ным шифрованием, защитой ключа HSM и другими функциями, предназначенными для чувствительных данных в регулируемых отраслях
IBM Business Process Manager (BPM)
IBM Cloud IaaS for compute and block storage
IBM Cloud IaaS for compute and block storage is a public cloud computing platform that offers a range of services, including those for compute, networking, storage, security and application development. Cloud administrators and users access IBM SoftLayer services over the Internet or through a dedicated network connection. IBMCloud IaaS for compute and block storageis largely considered infrastructure as a service (IaaS), a form of cloud computing in which a third-party provider hosts hardware, software and other infrastructure components on its users' behalf. For compute, IBM SoftLayer provides various bare-metal and virtual server configurations, along with an assortment of operating systems, hypervisors and database platforms. The virtual server configurations are available in either a single- or multi-tenant model, whereas the bare-metal server configurations are available in a single-tenant model only.
The ROI4CIO Product Catalog is a database of business software, hardware, and IT services. Using filters, select IT products by category, supplier or vendor, business tasks and problems. Find the right business solutions by using a neural network search based on the results of deployment products in other companies.