Enterprise Solutions Consulting Group (ESCG)
http://es-cg.info/
Information Technology
Description
Enterprise Solutions Consulting Group LLC, the privately owned business consulting firm that changes the ways that businesses acquire and retain clients.
Enterprise Solutions Consulting Group first opened its doors in Baku in 2010.
Enterprise Solutions Consulting Group LLC, specializes in providing high level consulting services in the area of Business Advisory, Information Management and System Integration. We support our clients ranging from SME to large companies in developing best practice business processes and implementing the underlying IT solutions.
Our young team of experienced professionals provides the innovation and energy so that your Company can focus on its core competencies and leave the IT, Infrastructure and Integration tasks to us.
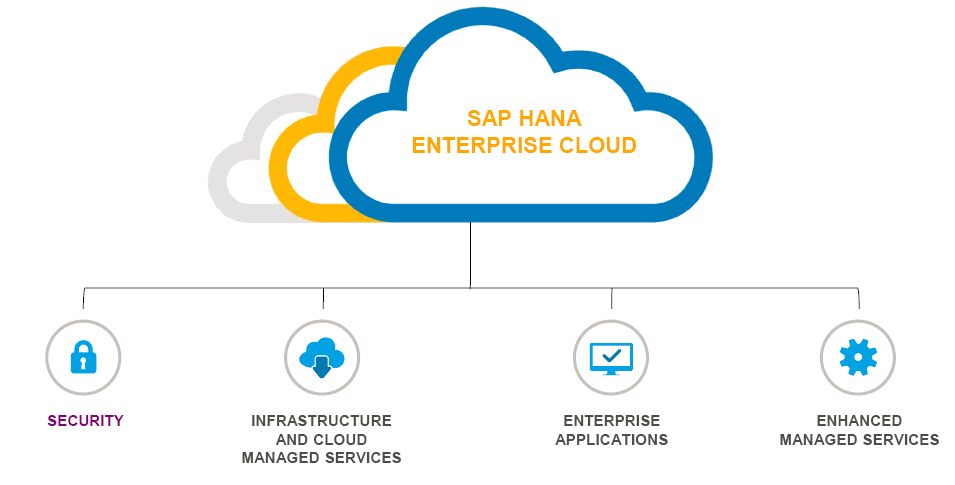
In addition, ESCG possesses extensive skills in all SAP and Oracle platforms typically involved in providing financial source data; e.g. HR, Finance, Supply Chain Management, Logistics, Controlling and Budgeting.
We offer innovative consulting services and can implement complex projects to increase the manageability, efficiency and competitiveness of our clients’ businesses.
Main area of services we provide are covering:
Business Process Optimization
Performance improvement and cost reduction
Internal controls optimization
Strategic Management
Centralization of main functions, shared service centers implementation
Supplied products
Partnership with vendors
Vendor | Partner status | Country | Partner types |
|---|---|---|---|
| SAP | Silver |