
Categories
Problems that solves
Unauthorized access to corporate IT systems and data
Risk or Leaks of confidential information
Risk of attacks by hackers
Risk of data loss or damage
Risk of lost access to data and IT systems
High costs
Values
Reduce Costs
Ensure Security and Business Continuity
NCP engineering IIoT Security
NCP engineering IIoT Security - secure communication of equipment, machines and systems.
About Product
Description
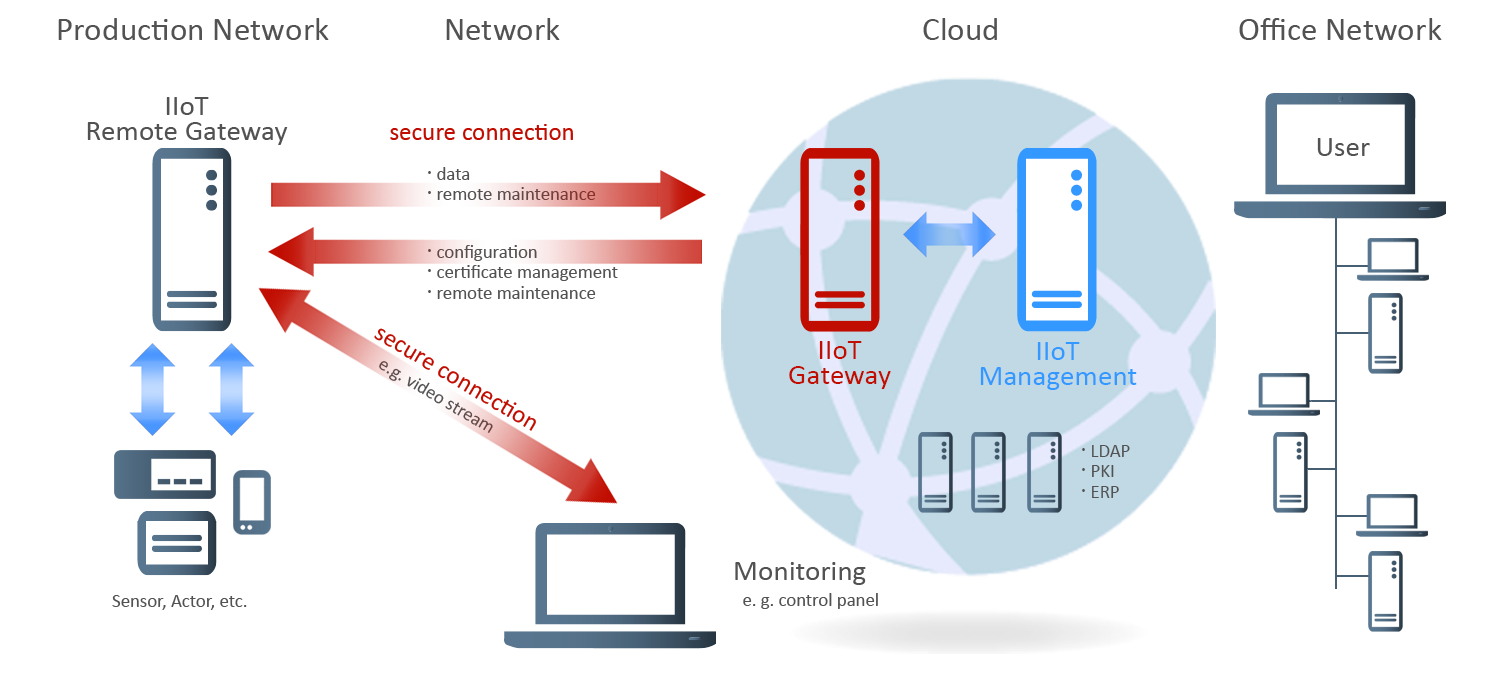
NCP has developed software components for secure data communication for Industrial Internet of Things (IIoT) scenarios. Several components at different points throughout the infrastructure bring back control and secure data encryption.
- IIoT Remote Gateway for secure communication of plant, machinery or systems
- Central IIoT Gateway for secure connection to IIoT Remote Gateways
- Management System for administration, monitoring and integration into existing infrastructures
- centrally managed machine certificates
- advanced Suite B Cryptography; for state-of-the-art data encryption and transfer
- standards-compliant
- easy integration into existing infrastructures
- centralized management of all components
- platform ready
- strong authentication
- support for virtualization
- the management system also for classic remote access VPN
Scheme of work
Competitive products
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
IT Security Department in company
















