
Categories
Problems that solves
Risk of data loss or damage
Risk of attacks by hackers
Malware infection via Internet, email, storage devices
Values
Ensure Security and Business Continuity
Manage Risks
About Product
Description
McAfee Active Response - Comprehensive endpoint detection and response.
McAfee Active Response delivers continuous detection of and response to advanced security threats to help security practitioners monitor security posture, improve threat detection, and expand incident response capabilities through forward-looking discovery, detailed analysis, forensic investigation, comprehensive reporting, and prioritized alerts and actions.
McAfee Active Response is proof of the effectiveness of the integrated McAfee security architecture, which is designed to resolve more threats faster and with fewer resources in a more complex world. McAfee Active Response gives you continuous visibility and powerful insights into your endpoints so you can identify breaches faster. And it provides you with the tools you need to correct issues faster and in the way that makes the most sense for your business. All of this power is managed via McAfee® ePolicy Orchestrator® (McAfee ePO™) software leveraging McAfee Data Exchange Layer—this provides unified scalability and extensibility without the need for incremental staff to administer the product.
Key Advantages
McAfee Active Response is proof of the effectiveness of the integrated McAfee security architecture, which is designed to resolve more threats faster and with fewer resources in a more complex world. McAfee Active Response gives you continuous visibility and powerful insights into your endpoints so you can identify breaches faster. And it provides you with the tools you need to correct issues faster and in the way that makes the most sense for your business. All of this power is managed via McAfee® ePolicy Orchestrator® (McAfee ePO™) software leveraging McAfee Data Exchange Layer—this provides unified scalability and extensibility without the need for incremental staff to administer the product.
Key Advantages
- Automated: Capture and monitor context and system state for changes that may be IoAs, as well as find dormant attack components, and send intelligence to analytics, operations, and forensic teams.
- Adaptable: When alerted, you can adjust to changes in attack methodologies; automate data collection, alerts, and responses to objects of interest; and customize your configuration to customer workflows.
- Continuous: Persistent collectors activate triggers on detection of attack events, alerting you and your systems to attack activity that you
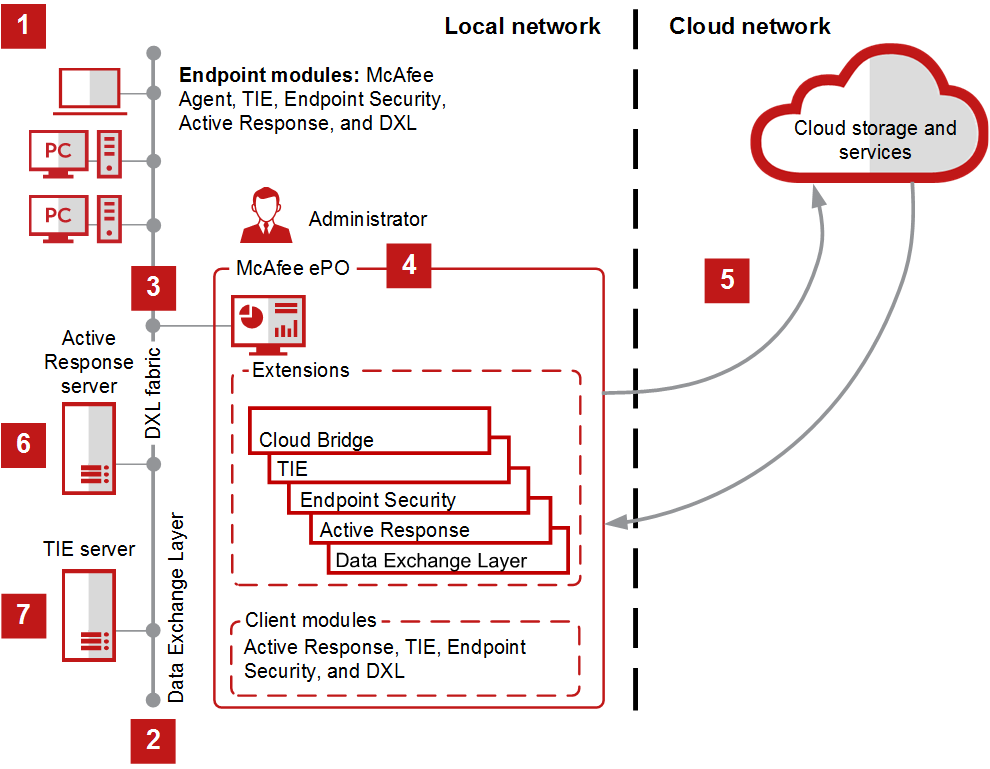
Scheme of work
Competitive products
Deployments with this product
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief Technical Officer
Chief IT Security Officer
Chief Sales Officer
Organizational Features
Web-based customer portal
Internet access is available for employees
GDPR Compliance





















