Categories
Problems that solves
Insufficient risk management
No control over implementation
Risk of data loss or damage
Risk of lost access to data and IT systems
No automated business processes
Risk or Leaks of confidential information
Unauthorized access to corporate IT systems and data
No control over data access
Values
Ensure Security and Business Continuity
Manage Risks
Ivanti Identity Director
IVANTI IDENTITY DIRECTOR: MODERN IDENTITY AND ACCESS MANAGEMENT SYSTEM FOR GREATER PRODUCTIVITY AND SECURITY
About Product
Description
Automating Onboarding and Offboarding
Today’s workforce is composed of people who may be fullor part-time, temporary, contractors, consultants, interns, pensioners, or retirees. With global employees working in multiple offices or remotely, safeguarding their identity—including characteristics and data attributes—is increasingly challenging and crucial to maintaining business security.
Automated onboarding provides access and provisions employees with services, applications, and devices. When employees’ roles or responsibilities change, access is adjusted automatically as needed. When people leave an organization, automated offboarding ensures quick and efficient cancellation of account access and privileges, while ensuring policy consistency and reducing the risk of security breaches.
Ivanti® Identity Director, an attribute-based identity management solution, empowers IT staff to manage identities and access to company resources easily and expertly. It gives employees the right levels of access based on identity and enables them to stay productive while the business remains secure.
One Solution, Many Uses
An employee’s identity is central to many other aspects of enterprise IT. Common ways enterprises leverage Ivanti
Identity Director include:
Identity Director include:
- Identity Management: IT can provision the right access to services and apps—based on identity attributes—and then modify access based on attribute privileges throughout the entire identity lifecycle.
- Auditable Compliance: Supports the need to demonstrate compliance with regulatory data-protection standards such as GDPR, HIPAA, and PCI.
- Infrastructure Automation: IT can consolidate, control, and enforce access privileges, no matter where apps are hosted. With the visibility to centrally troubleshoot, you are future-proofed with automation to simplify infrastructure or process changes.
- Security Risk Mitigation: Automate and streamline provisioning and deprovisioning processes to eliminate human error, enforce security policies, and reduce “shadow IT.”
- User Self-Service: Offer self-service and a mobile app for workers to request access and other common IT services.
- Access Control – Manage access based on identity attributes and context-aware policies to maintain worker productivity and business security.
- Automated Delivery and Return – Automate the delivery of predictable services to the business when needed, based on policy and workflows.
- Flexible Administration – Simplify the management of your complex hybrid environment with connectors to help with service delivery and return in both on-premises and cloud systems.
- Governance – Reduce risk and ensure compliance through insight into delivery and return processes through transaction analytics and audit trail. Easy access to audit trails and reports simplifies audit reporting and reduces the manual-attestation tasks associated with meeting governance requirements.
- Self Service – Deliver services to the business when requested via a self-service portal or mobile app.
- Single-Sign-On – Provide end users one-click access directly to vendors, without presenting credentials each time.
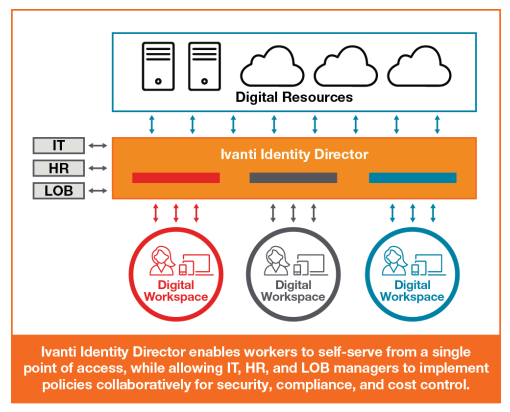
- Identity Warehouse – Identity Director’s central identity warehouse aggregates digital resources from existing systems, enabling IT to deliver predictable services to the business automatically when needed.
Scheme of work
Competitive products
Deployments with this product
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
GDPR Compliance
Internet access is available for employees
Сonfidential data