
Problems that solves
Unauthorized access to corporate IT systems and data
Risk or Leaks of confidential information
Malware infection via Internet, email, storage devices
Non-existent or decentralized IT incidents' management
Risk of attacks by hackers
Risk of lost access to data and IT systems
Risk of data loss or damage
Insufficient risk management
Values
Ensure Security and Business Continuity
Centralize management
Manage Risks
About Product
Description
VMware Carbon Black Cloud is a cloud native endpoint and workload protection platform (EPP and CWP) that combines the intelligent system hardening and behavioral prevention needed to keep emerging threats at bay, using a single lightweight agent and an easy-to-use console. By analyzing more than 1 trillion security events per day, VMware Carbon Black Cloud proactively uncovers attackers’ behavior patterns and empowers defenders to detect and stop emerging attacks. As a key means to realizing intrinsic security, VMware Carbon Black Cloud simplifies and strengthens your approach to security across any app, any cloud, and any device.
Adaptive Prevention Delivers Better Protection
The majority of today’s cyberattacks feature advanced tactics such as lateral movement and island hopping that target legitimate tools to inflict damage. These sophisticated hacking methods pose a tremendous risk to targets with decentralized systems protecting high-value assets, including money, intellectual property and state secrets.
VMware Carbon Black CloudTM thwarts attacks by making it easier to:
Gain 24-hour visibility from our security operations center of expert analysts, who provide validation, context into root cause and automated monthly executive reporting. Audit and remediation – real-time device assessment and remediation Easily audit the current system state to track and harden the security posture of all your protected devices. Enterprise EDR – threat hunting and containment Proactively hunt for abnormal activity using threat intelligence and customizable detections.
- Analyze billions of system events to understand what is normal in your environment
- Prevent attackers from abusing legitimate tools
- Automate your investigation workflow to respond efficiently
Gain 24-hour visibility from our security operations center of expert analysts, who provide validation, context into root cause and automated monthly executive reporting. Audit and remediation – real-time device assessment and remediation Easily audit the current system state to track and harden the security posture of all your protected devices. Enterprise EDR – threat hunting and containment Proactively hunt for abnormal activity using threat intelligence and customizable detections.
Scheme of work
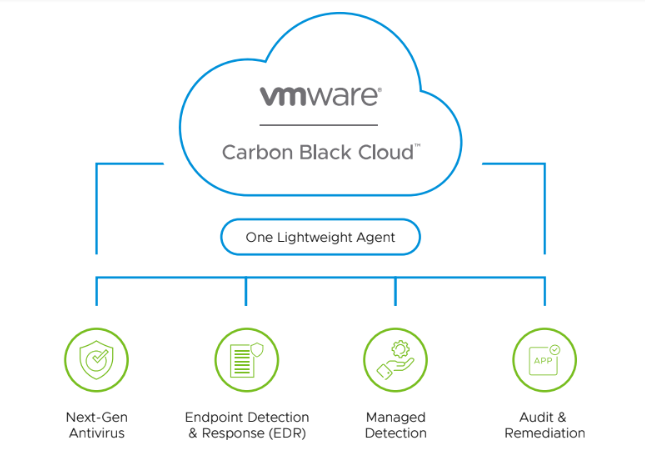
Deployments with this product
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
IT Security Department in company
Сonfidential data
Internet access is available for employees
GDPR Compliance

