Problems that solves
No IT security guidelines
Risk or Leaks of confidential information
Insufficient risk management
Values
Ensure Security and Business Continuity
Manage Risks
About Product
Description
In the human brain, the cerebellum receives information from the sensory systems, the spinal cord, and other parts of the brain and then regulates motor movements. The cerebellum coordinates voluntary movements, resulting in smooth and balanced muscular activity. It is also important for learning motor behaviors. The Veracity “Cerebellum” platform is designed to serve a similar function for industrial networks.
Veracity’s Cerebellum provides a system level approach that responds to sensory data and orchestrates the pre-designed production process response.
Cerebellum is designed for operational and engineering efficiency; a logical workflow-based approach to network configuration, orchestration, security and resilience. What Does Veracity Cerebellum Offer:
Security Level Model
Security Zone Management
Veracity’s Cerebellum provides a system level approach that responds to sensory data and orchestrates the pre-designed production process response.
Cerebellum is designed for operational and engineering efficiency; a logical workflow-based approach to network configuration, orchestration, security and resilience. What Does Veracity Cerebellum Offer:
Security Level Model
- Cerebellum provides the first fully functional visual based security level model builder.
- The security level allows for a user to quickly build the Purdue Manufacturing Model, ISA-95, ISA-99, or even create a model from scratch.
- The user can quickly define the functional levels in their model and drag & drop device types from the industry library to their respective functional levels.
- Finally, the user can easily define rules for each level (e.g. communication between levels)
- Cerebellum makes device management simple.
- With Veracity’s INDUSTRIAL SDN™, 100% of all devices connected to the network are identified.
- During the learning/identification mode, the system is also characterizing the network devices to classify the functional role and device type (e.g., PLC, RTU, SCADA Server, etc.).
- Device management provides information to the user to define whether a device should be authorized or not.
- The user can also decide to quarantine a device (e.g., an unauthorized integrator laptop).
Security Zone Management
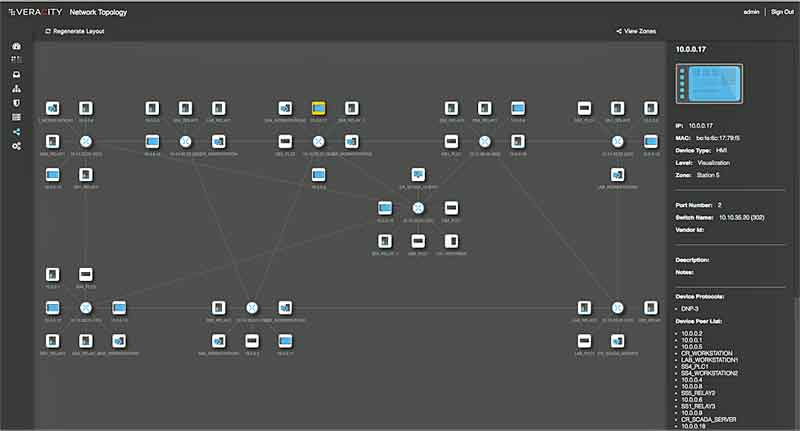
- Cerebellum provides an innovative approach to network segmentation via the creation of security zones.
- This workflow-based approach allows the user to easily create security zones or logical groups and assign devices to those groups.
- This can be accomplished in multiple ways from Cerebellum’s single pane of glass – by asset/network drag and drop or command line interface.
- Cerebellum provides an innovative approach to traffic engineering which the abstracts complexity at scale while allowing fine-grained control.
- The user can manage traffic at a high level – e.g. what zone to zone communications are permitted – or via very granular rules such as “a specific PLC is allowed to communicate with a specific HMI over DNP-3.”
- Where engineers are very comfortable working with spreadsheet-like interfaces for managing complex data, what is lacking is a visual representation.
- Visual validation is an important step to identify the rules that are being configured in a simplified and consumable manner.
- This enables the user to maximize their efficiency and accuracy.
- In addition to simplified traffic engineering via zones and device types, Cerebellum provides dynamic, API-based control by allowing configuration change sets to be grouped as policies.
- These policies can be enabled or disabled at any time, vastly simplifying operational workflows.
- For instance, during normal operation it may not be required to allow engineering workstations network access to control (e.g., PLCs) devices.
- The system will support both a default policy of denying that access alongside an operational policy of allowing that access, and switching between them can be done via a remote but authorized process driven by a change management workflow or via a few clicks in the user interface.
Scheme of work
Competitive products
Deployments with this product
User features
Roles of Interested Employees
IT Security and Risk Management
Chief IT Security Officer
Chief Information Officer
Organizational Features
IT Security Department in company
Сonfidential data
GDPR Compliance