Categories
Problems that solves
Shortage of inhouse software developers
Shortage of inhouse IT resources
High costs of IT personnel
Shortage of inhouse IT engineers
Values
Ensure Security and Business Continuity
Reduce Costs
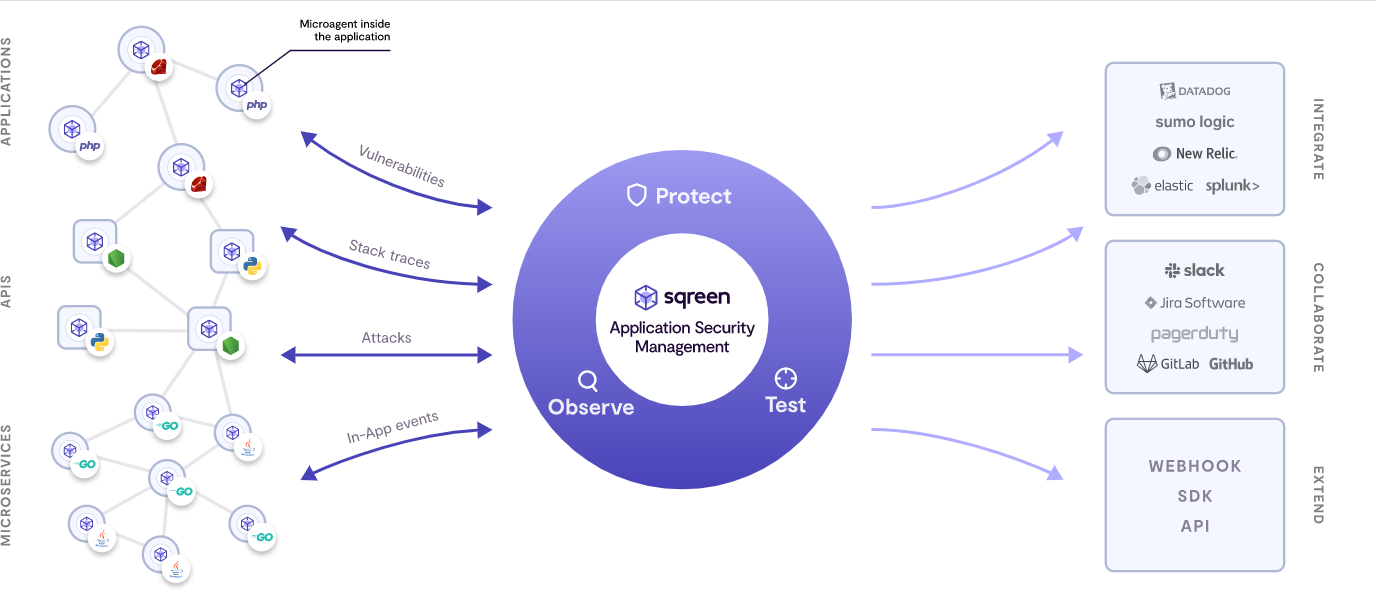
Sqreen Platform
With Sqreen, organizations of all sizes, can strengthen their application security, decrease the number of security incidents, and resolve incidents more quickly when they do occur.
About Product
Description
Application security platform for the modern enterprise
As opposed to static pattern-based approaches, Sqreen analyses application execution logic in real time to deliver more robust security without compromising performance. This empowers security owners to easily extend protection and visibility across their entire application portfolio without requiring on-going maintenance and tuning.
- Protect. Protect applications by preventing data breaches, stopping account takeovers and blocking business logic attacks.
- Observe. Increase visibility by monitoring incidents in real time, streamlining incident response management and automating your application inventory.
- Test. Secure code by finding critical threats, fixing vulnerabilities and integrating security into the SDLC.
- Block attacks from the OWASP top 10, including Cross-Site Scripting (XSS), SQL injections, or Server-Side Request Forgery (SSRF).
- Combine multiple protections into one: RASP (Runtime Application Self-Protection), In-App WAF (Web Application Firewall), Account Takeovers, and more.
- Leverage the full execution context of requests and block critical attacks without generating false positives.
- Prevent business logic attacks with out-of-the-box playbooks that cover feature abuses, shared users accounts and more.
- Deploy Sqreen's microagents in minutes on any type of architecture.
- Continuously adapt protections to your evolving application's stack without manual configurations required.
- Don't block legitimate traffic or slow down your engineers.
- Integrate Sqreen into your workflow with native integrations, webhooks, and APIs.
- Always stay one step ahead of attackers with incidents alerting you in real-time only in case of a critical attack.
- Go beyond an IP and investigate malicious activities by linking security activities to authenticated users.
- Fasten vulnerability remediation with stacktraces pinpointing the vulnerable line of code.
- Drill down into user and IP activity timelines to identify attackers before they cause harm.
Scheme of work