Categories
Problems that solves
Unauthorized access to corporate IT systems and data
Risk or Leaks of confidential information
Malware infection via Internet, email, storage devices
Non-compliant with IT security requirements
Values
Ensure Security and Business Continuity
Skybox Horizon
Skybox Horizon is the only solution that combines data integration, comprehensive network modeling and attack vector analytics with visualization technology
About Product
Description
Skybox® Horizon gives security leaders a simple picture of their organization’s entire attack surface. But behind this picture is a heavily detailed, interactive model giving you fast insight to your biggest cyber risks.
With this insight and systematic prioritization, you can quickly eliminate imminent threats, while continuously monitoring potential threats.
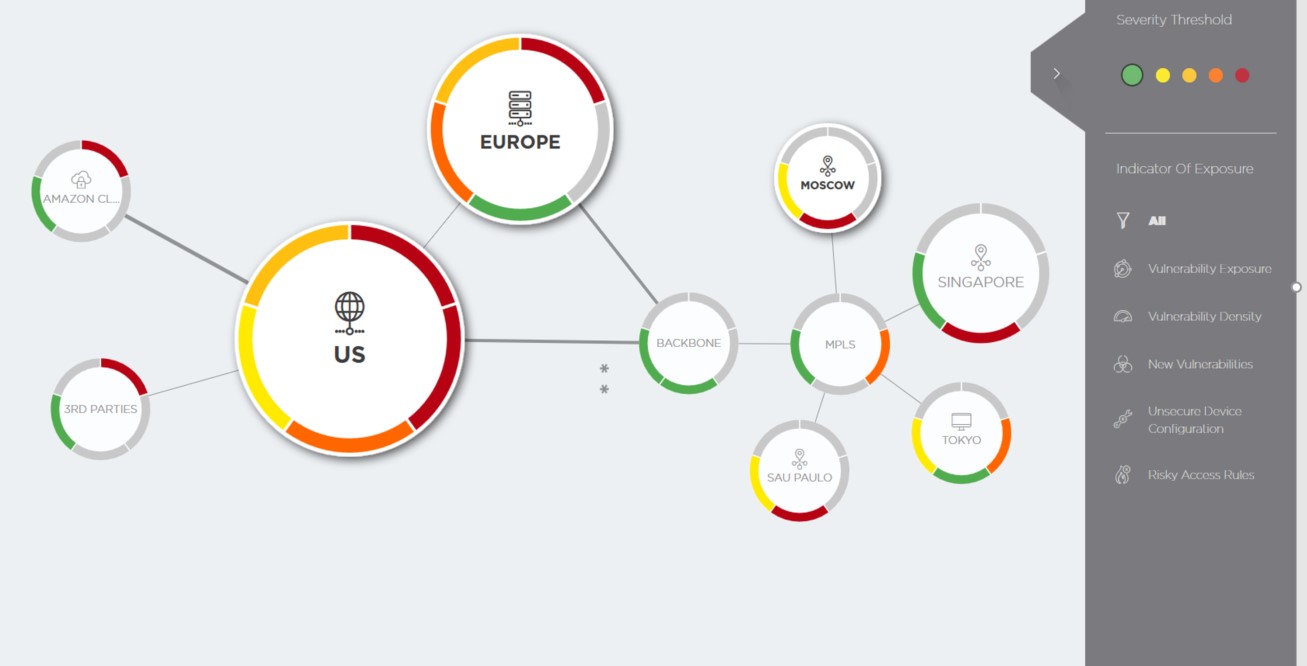
Horizon isn’t just a topology map. It’s the product of intelligence from the entire Skybox® Security Suite in a single pane of glass. Horizon provides an abstracted view of the deeper Skybox model that includes hybrid network topology — across on–prem, multi–cloud and operational technology (OT) environments — security controls, assets, vulnerabilities and threats. BENEFITS OF SKYBOX HORIZON Unifies Data in a Simple Picture
Horizon isn’t just a topology map. It’s the product of intelligence from the entire Skybox® Security Suite in a single pane of glass. Horizon provides an abstracted view of the deeper Skybox model that includes hybrid network topology — across on–prem, multi–cloud and operational technology (OT) environments — security controls, assets, vulnerabilities and threats. BENEFITS OF SKYBOX HORIZON Unifies Data in a Simple Picture
- Consolidates data silos from endpoint and network security products, including physical IT, multi–cloud and OT networks
- Incorporates data provided by vendors and Skybox® Research Lab intelligence of exploits in the wild and available exploit code
- Creates a map of servers, endpoints, security and networking devices and hybrid network topology and gives insights to security exposures
- Quickly shows exposed vulnerabilities and vulnerability exploit status based on intelligence from the current threat landscape
- Prioritizes IOEs to reflect the risk and likelihood of an attack
- Filters IOEs by types and severity level for dynamic analysis
- Identifies vulnerabilities that pose the most risk across the entire enterprise, based on your attack surface and the threat landscape
- Distinguishes between real exposures and security issues that are effectively mitigated by compensating controls
- Enables security leaders to direct resources to patching or remediating systems and applications most at risk
- Develops a common understanding of risks and remediation priorities across technical and business groups
- Justifies security investments to CEO and CFO
- Tracks and reports on progress toward strategic security or compliance goals with IOE trends or historical comparisons
Scheme of work
Competitive products
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief Technical Officer
Chief IT Security Officer
Organizational Features
Internet access is available for employees
Company branches in different countries
GDPR Compliance