
Categories
Problems that solves
Risk of data loss or damage
Risk of lost access to data and IT systems
Complex and non-transparent business processes
Shortage of information for decision making
Values
Ensure Security and Business Continuity
Manage Risks
About Product
Description
Know Your Weak Points
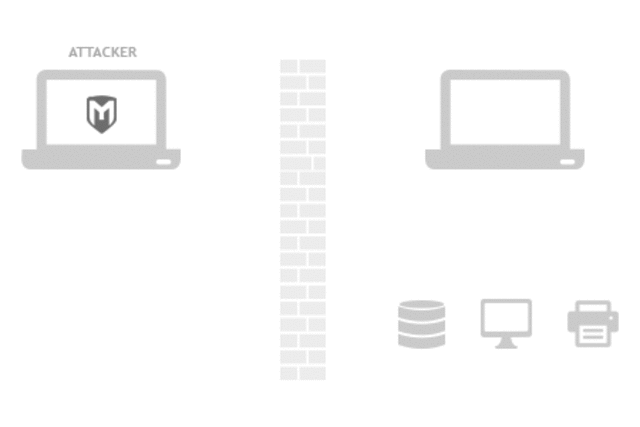
It’s vital to find your vulnerabilities before a malicious attacker does.
Utilize world's largest exploit database
Leading the Metasploit project gives Rapid7 unique insights into the latest attacker methods and mindset. Rapid7 works with the community to add an average of 1 new exploit per day, currently counting more than 1,300 exploits and more than 2,000 modules.
Simulate real-world attacks against your defenses
Metasploit evades leading anti-virus solutions 90% of the time and enables you to completely take over a machine you have compromised from over 200 modules. Pivot throughout your network to find out just how far an attacker can get.
Uncover weak and reused credentials
Test your network for weak and reused passwords. Going beyond just cracking operating system accounts, Metasploit Pro can run brute–force attacks against over 20 account types, including databases, web servers, and remote administration solutions. In addition, it can utilize specialized tools designed to expose credentials' scope and effectively gauge impact of an exposed credential.
Prioritize What Matters Most
Finding your weak points is only half the battle. As a penetration tester, it is your job to perform a thorough assessment and communicate what needs to be done to reduce the risk of a breach.
Pinpoint weak links in the attack chain
Attacks are more sophisticated today; the adversary is using multiple techniques combined to breach your systems faster than ever. With Metasploit Pro, you can simulate attacks like the adversary and easily report the biggest security risks.
Closed-loop integration with Nexpose for remediation
When other departments question the validity of scan results, demonstrate that a vulnerability puts systems and data at risk of compromise. You'll get quick buy–in for remediation measures and build credibility with stakeholders. Metasploit and Nexpose provide the only closed-loop validation solution from a single vendor that simplifies vulnerability prioritization and remediation reporting.
Drive Better Security Program Development
Time is of the essence. Automation, proactive user education, and advanced reporting will enhance your team’s efficiency, productivity, and success.
Run penetration projects at scale
Conducting an assessment and managing data in networks with over 100 hosts can be challenging. Metasploit Pro scales to support thousands of hosts per project on engagements and multiple penetration testers. Automate penetration testing steps with Task Chains and MetaModules to improve productivity.
Reduce user risk using phishing campaigns and education
Send and track emails to thousands of users with Metasploit Pro's scalable phishing campaigns. Clone web application login pages with one click to harvest credentials. Measure conversion rates at each step in the phishing campaign funnel. When users take a dangerous action, they can be redirected to a training site on the spot. With InsightUBA, any users who have been phished will also be automatically added to the InsightUBA watch list.
Complete compliance programs faster
Generate reports to show your findings and sort them by regulations such as PCI DSS and FISMA. Verify that remediations or compensating controls implemented to protect systems are operational and effective. Create vulnerability exceptions based on hard evidence that easily pass your next audit. Automatically record actions and findings from your network and application–layer assessment to save valuable time otherwise spent on cutting and pasting.
Scheme of work
Competitive products
Deployments with this product
User features
Roles of Interested Employees
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
IT outsourcing is used
Сonfidential data
Legal requirement to backup data

















