
Categories
Problems that solves
Malware infection via Internet, email, storage devices
Risk of attacks by hackers
Risk of data loss or damage
Risk of lost access to data and IT systems
Values
Reduce Costs
Ensure Security and Business Continuity
Appraise and Train Staff
About Product
Product presentation
Description
Advanced, consolidated endpoint defense McAfee Endpoint Security delivers industry-leading protection and operational simplicity for your diverse endpoint environment. Core threat prevention Essential anti-virus, exploit prevention, firewall, and web control communicate with each other. Machine learning State-of-the art techniques identify malicious code based on appearance and behavior. Application containment Limit the impact of suspicious files and zero-day malware by blocking behaviors and containing them before they can infect or spread in your environment. Endpoint detection and response Our integrated, automated, and adaptable endpoint detection and response (EDR) technology is easy to use and makes incident response as simple as a single click.
Product features
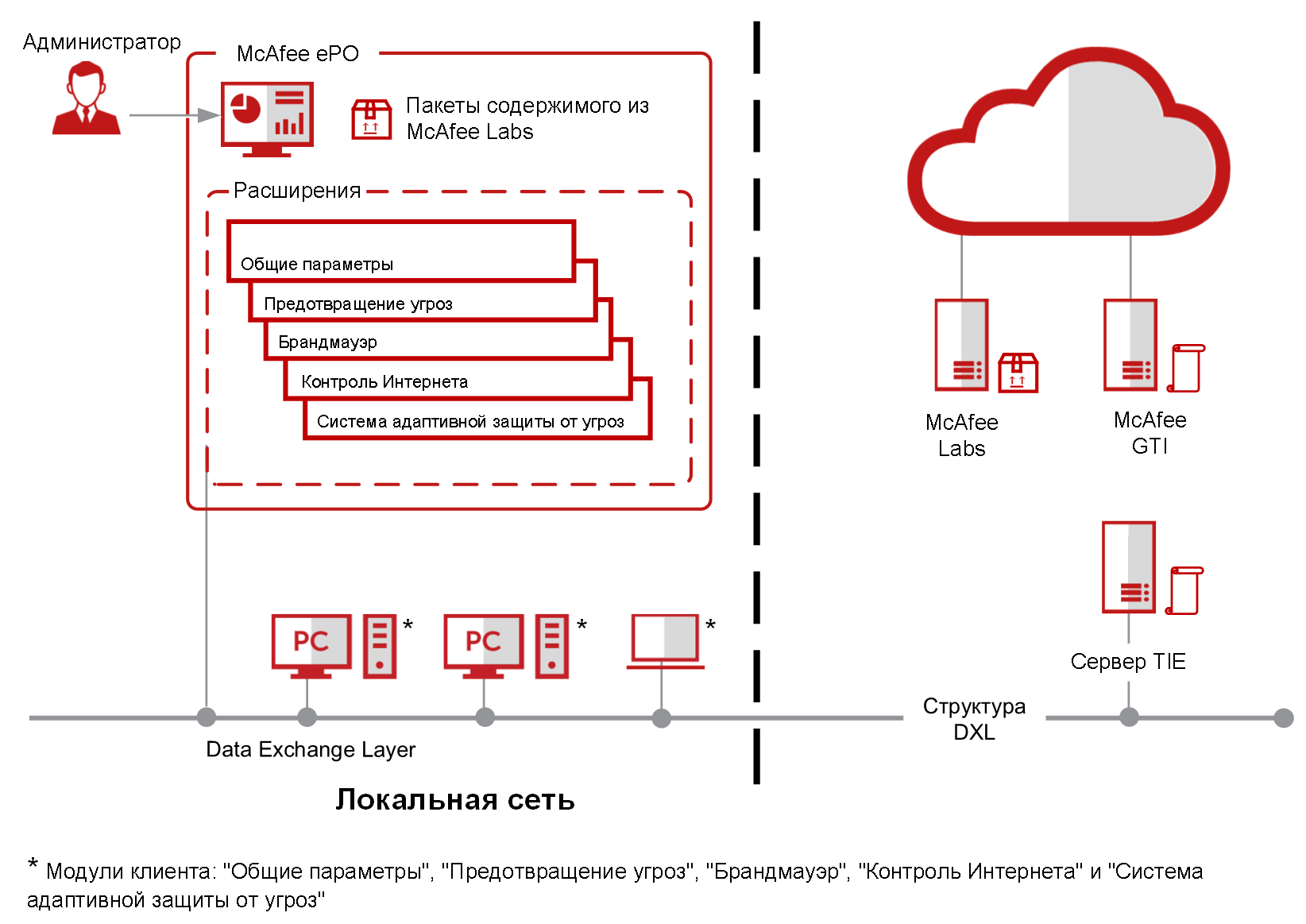
- Centralized management. The McAfee ePolicy Orchestrator management console can be deployed on premises or in the cloud. It provides greater visibility, simplifies operations, boosts IT productivity, unifies security, and reduces costs.
- Advanced anti-malware protection. Our anti-malware engine is continually updated by McAfee Global Threat Intelligence and works efficiently across multiple operating systems.
- Machine learning analysis. Detect zero-day threats in near real time by examining how they look and behave to halt threats designed to evade detection.
- Dynamic application containment. Defend against ransomware and greyware by securing endpoints that are leveraged as entry points for attacks.
- Proactive web security. Ensure safe browsing with web protection and filtering for endpoints.
- Actionable threat forensics. Quickly see where infections are, why they are occurring, and the length of exposure to understand the threat and react more quickly.
Scheme of work
Competitive products
Deployments with this product
User features
Roles of Interested Employees
Chief Information Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
Internet access is available for employees
GDPR Compliance
























