Problems that solves
Inability to forecast execution timelines
Unauthorized access to corporate IT systems and data
Risk or Leaks of confidential information
No monitoring of corporate IT processes
Risk of lost access to data and IT systems
Risk of data loss or damage
Customer fraud
No control over implementation
Values
Reduce Costs
Ensure Security and Business Continuity
Ensure Compliance
Manage Risks
About Product
Description
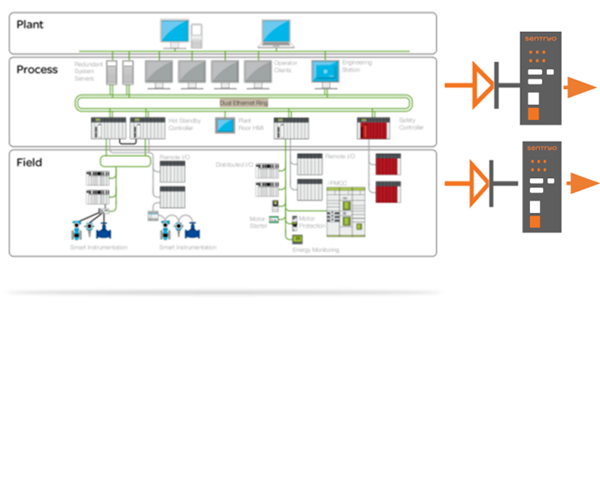
It provides control engineers with a detailed view of all equipment in their industrial infrastructures and their vulnerabilities, records each equipment modification in order to identify the source of an attack and detects behavior anomalies in real time to raise the alarm and collaborate with IT to fight against cyber attacks.
ICS CyberVision combines Deep Packet Inspection mechanisms to understand what’s happening on your network, a knowledge base updated daily by Sentryo security researchers, Artificial Intelligence algorithms to extract relevant information, and Machine Learning to detect anomalies. The essential tool for controlling the security of your OT infrastructure
Instant & Automatic visibility of all industrial components, logical connections and weaknesses:
Intuitive and visual representation of industrial systems offering a tailored view and fostering collaboration:
ICS CyberVision combines Deep Packet Inspection mechanisms to understand what’s happening on your network, a knowledge base updated daily by Sentryo security researchers, Artificial Intelligence algorithms to extract relevant information, and Machine Learning to detect anomalies. The essential tool for controlling the security of your OT infrastructure
- Visibility:automatic OT assets inventory that also highlights network flows and equipment vulnerabilities
- Integrity:track configuration changes and record all key events to identify the source of an attack
- Security: detect abnormal behaviors to raise alarms and show events in an OT language facilitating decision making
- IT/OT Collaboration: integrate with firewalls, SIEM, CMDB to automate incident response & include OT in your IT security strategy
Instant & Automatic visibility of all industrial components, logical connections and weaknesses:
- Real-time risk profile and reduced exposure to cyber attacks
- Capability to build an effective action plan and make more informed decisions
- Adapted and effective allocation of resources
- Anticipate operational incidents
- Reduced risk of operational incidents
- Minimized downtime
- Fully passive approach with no impact on the control system
- Instant detection and response to cyber threats
- Reliable and trustworthy network
- Higher productivity and quality of service
- Saving time and money by focusing on protecting the most critical parts of the business first
Intuitive and visual representation of industrial systems offering a tailored view and fostering collaboration:
- Intuitive, interactive and user-friendly platform
- Designed for OT people such as Control Engineers
- Rich and contextualized events
- Clarity of key roles and responsibilities
- Tools for both the OT staff and Cybersecurity experts
Scheme of work
Competitive products
Deployments with this product
User features
Roles of Interested Employees
Chief Executive Officer
Chief Information Officer
Chief Technical Officer
Chief IT Security Officer
IT Security and Risk Management
Organizational Features
IT Security Department in company
Internet access is available for employees
GDPR Compliance