Problems that solves
No IT security guidelines
Unauthorized access to corporate IT systems and data
Risk or Leaks of confidential information
Malware infection via Internet, email, storage devices
Risk of attacks by hackers
Risk of data loss or damage
Risk of lost access to data and IT systems
Non-compliant with IT security requirements
Values
Reduce Costs
Ensure Security and Business Continuity
Ensure Compliance
F5 Big-IP Application Security Manager
A comprehensive web application firewall that protects apps and data from known and unknown threats, defends against bots that bypass standard protections, and virtually patches app vulnerabilities.
About Product
Description
Protect your organization and its reputation by maintaining the confidentiality, availability, and performance of the applications that are critical to your business with F5 Web Application Firewall (WAF) solutions.
F5 WAF solutions are deployed in more data centers than any enterprise WAF on the market. The comprehensive suite of F5 WAF solutions includes managed rulesets for Amazon Web Services (AWS); cloud-based, self-service, and managed service in the F5 Silverline cloud-based service delivery platform; application delivery controller (ADC) integration with F5 BIG-IP Application Security Manager (ASM); and F5 Advanced Web Application Firewall (Advanced WAF).
Advanced WAF redefines application security to address the most prevalent threats organizations face today:
- Automated attacks and bots that overwhelm existing security solutions.
- Web attacks that steal credentials and gain unauthorized access across user accounts.
- Application layer attacks that evade static security based on reputation and manual signatures.
- New attack surfaces and threats due to the rapid adoption of APIs.
- Protect web and mobile applications from malicious bots;
- Safeguard credentials and sensitive data from theft and abuse;
- Defend against sophisticated application denial-of-service (DoS);
- Mitigate sophisticated threat campaigns;
- Protect APIs;
- Ensure application security and compliance;
- Turn on protection immediately;
- Patch vulnerabilities fast;
- Deploy flexibly;
- Defend with proven advanced protections;
- Magnify threat knowledge.
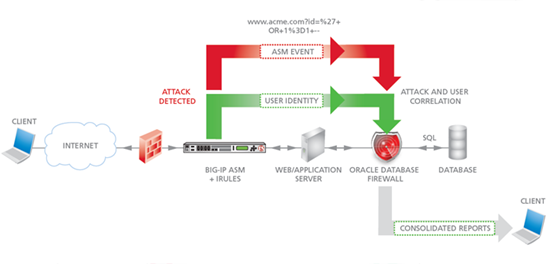
Scheme of work