Problems that solves
No control over data access
No IT security guidelines
Unauthorized access to corporate IT systems and data
Risk or Leaks of confidential information
Employee personal use of corporate IT during working hours
Risk of data loss or damage
Risk of lost access to data and IT systems
Customer fraud
Values
Reduce Costs
Ensure Security and Business Continuity
Exabeam Advanced Analytics
Exabeam Advanced Analytics is the world’s most-deployed UEBA solution - Modern threat detection using behavioral modeling and machine learning.
About Product
Description
Complex Threat Identification with Behavioral Analysis
Cyberattacks are becoming more complex and harder to find. Often correlation rules can’t find the attacks because they lack context or miss incidents they’ve never seen — generating false negatives. Correlation rules also require much maintenance. Advanced Analytics automatically detects the behaviors indicative of a threat. Now teams don’t have to spend time with frequently faulty correlation rules.
Prebuilt Timelines Automatically Reconstruct Security Incidents
Analysts shouldn’t spend days or weeks gathering evidence and constructing timelines of incidents by querying and pivoting through their SIEM. With Advanced Analytics, a prebuilt-incident timeline flags anomalies and displays details of the incident for the full scope of the event and its context. Now analysts can stop spending time combing through raw logs to investigate incidents. What took weeks to investigate in a legacy SIEM can now be done in seconds.
Dynamic Peer Grouping
User behavior patterns often differ based on a myriad of attributes, including: the team they are on, what projects they are involved in, where they are located, and more. Thus, behavioral baselines shouldn’t be static. Dynamic peer grouping uses machine learning to assign users to groups based on their behavior, then to compare their activity against that of those groups to identify anomalous, risky behavior.
Lateral Movement Detection
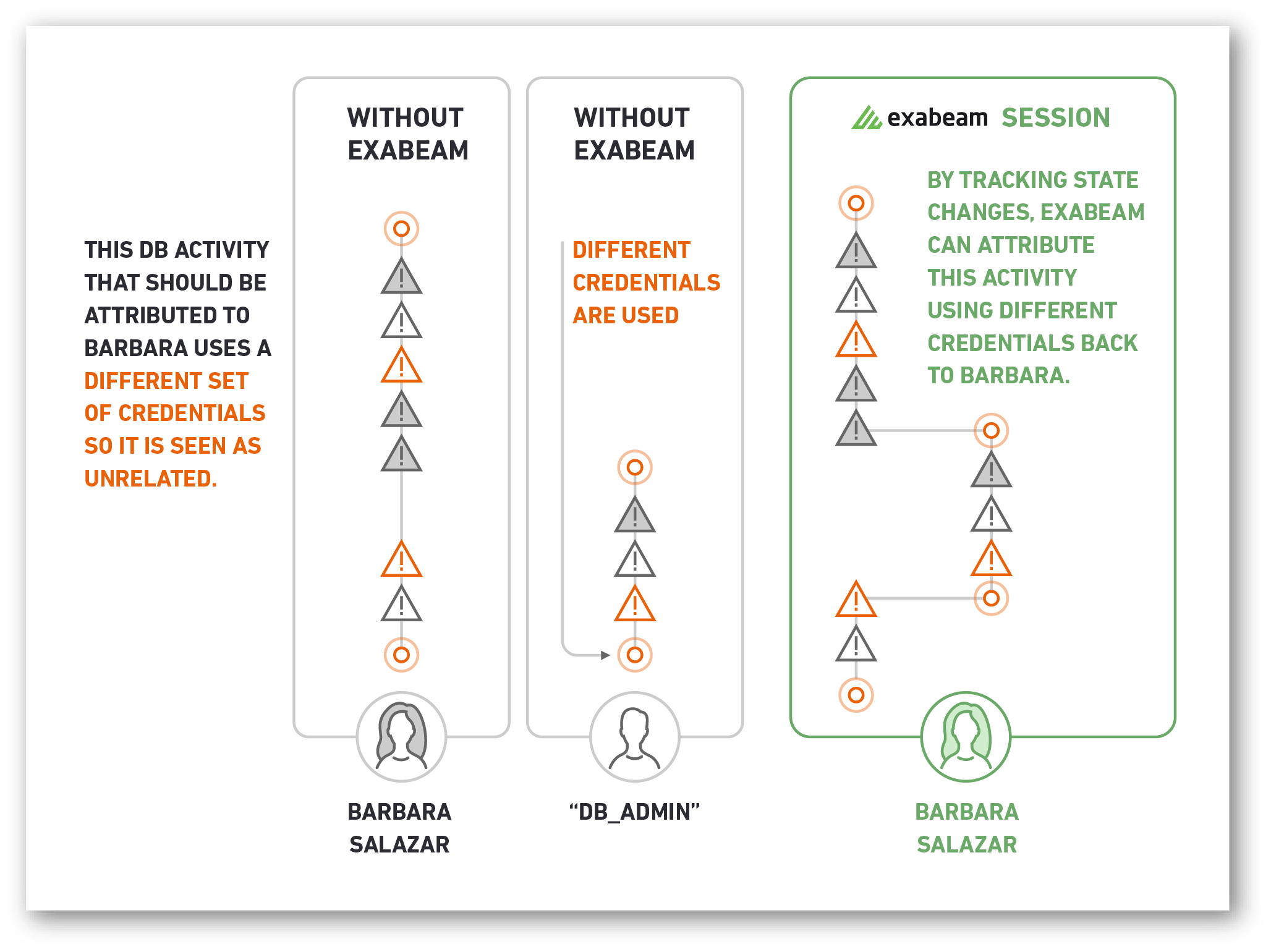
Lateral movement is a method attackers use to move through a network by using IP addresses, credentials, and machines in search of key assets. Tracking is difficult because the trace information only tells part of the story. Data must be analyzed from everywhere, linking the attack to the source. The Advanced Analytics patented technology tracks suspected activities even if there are changes to devices, IP addresses, or credentials.
Asset Ownership Association
Another time-intensive part of performing a security investigation is the manual process of determining who owns or regularly uses the devices involved in an incident. There isn’t a convenient IT database linking devices to their owners, and mobile devices can exist outside of any tracking. Advanced Analytics is able to determine the owner of a device based on their pattern of behavior and interactions.
Scheme of work