Categories
Problems that solves
Unauthorized access to corporate IT systems and data
Risk or Leaks of confidential information
Malware infection via Internet, email, storage devices
Risk of attacks by hackers
Risk of data loss or damage
Insufficient risk management
Non-compliant with IT security requirements
Values
Ensure Security and Business Continuity
Ensure Compliance
Manage Risks
Coronet SecureCloud
Autonomous, all-in-one platform that protects corporate cloud applications from unauthorized access, prevents data leakage, and mitigates cloud threats.
About Product
Description
True cloud security must ensure users are authenticated, that the device used is not compromised, that the network used is safe, and yes, that the user behavior (Access, downloads, uploads, collaboration, reporting) is allowed.
To ensure true cloud security, organizations must purchase, integrate, and operate multiple platforms - which is very expensive, very complicated, labor intensive, and extremely time consuming.
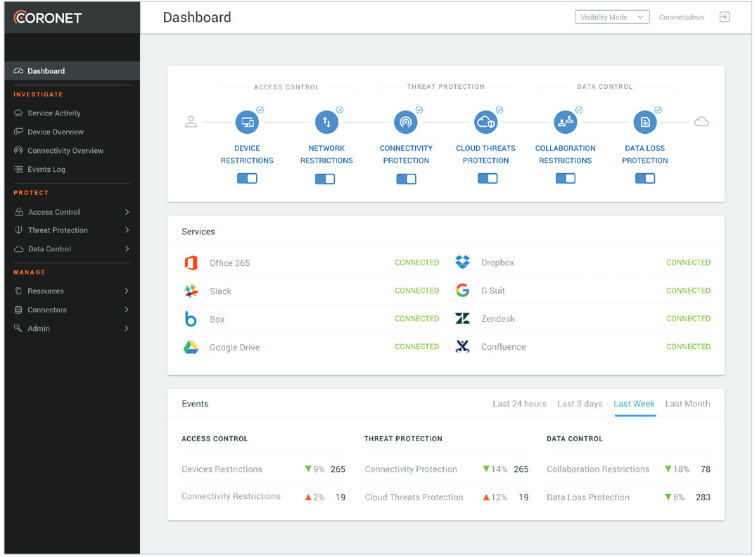
SecureCloud platform tackles this problem by providing continuous, real time visibility, control and remediation, Coronet SecureCloud ensures that corporate data is used only by trusted users, using trusted devices, connecting through trusted networks to trusted cloud services.
Threat Protection
- Ensure Control over who has access to the cloud platforms, and where from
- Ensure GDPR, HIPPA, SOX, compliance, and detect PII, PHI, and EDR automatically
- Block compromised devices from accessing corporate data in the cloud resources
- Control what users can do, and who they can collaborate with
- Prevent malware spread through cloud usage (such as file sharing)
- Provide visibility into activity in the cloud, the devices used, and the data that was shared
- Detect and mitigate advanced cloud-to-cloud attacks
SecureCloud device authentication
With SecureCloud, an organization can not only enforce fine-grained access control to a cloud service, but also create and enforce a policy that prohibits access from unmanaged devices with no active Coronet agent running. SecureCloud uses federated user authentication processes, such as SAML, that put the SecureCloud service in the path of SaaS applications. Each authentication request is steered to the SecureCloud authentication proxy that performs pre-authentication risk assessment based on user, device and service security postures and makes context-based access decisions.Location based defense
Many organizations require that sensitive information and services only be accessed on premises or in secure locations. SecureCloud includes sophisticated location resources management and turns raw geo-location data into geo-spatial intelligence, leveraged in access control, threat prevention and data control.Threat prevention
Additionally, the administrator can mark a named location as trusted or risky (white and black list). For a conditional access policy, the trusted or risky locations are yet another filter options available for conditional access policy definition. Named locations are also important for the reduction of false positives during detection of impossible travel and atypical locations risk events. SecureCloud identifies, mitigates, and automatically remediates threats across cloud services. It monitors activity patterns in the cloud, determines the behavioral models and establishes baselines. Upon connection of a cloud service, all cloud activity is scored according to various predefined risk factors. SecureCloud inspects every user session and takes automatic remediation actions when something happens that is different from either the baseline or from the user’s regular activity. In this manner, SecureCloud continues evolving its models as it observes new and often unusual behavior without human intervention. These capabilities set SecureCloud apart from traditional approaches that require an unreasonable number of manual updates to ensure accurate threats detection.Scheme of work